Update
Update 2023/09/10
The vulnerability has been included and approved for public disclosure by MITRE.
Vuln_Author: WEI(ギカク)
The program is built using the xmapp-php8.2.4 version
Simple Book Catalog App
This project used a basic CRUD (Create, Read, Update and Delete) that has image upload for books.
Overview of the App:
The PHP Book Catalog App is a web-based application designed to help users manage and organize their collection of books. The app allows users to perform the following tasks:
- Add Books: Users can add new books to the catalog by providing details such as book title, author, category, image, and abstract.
- Update Books: Users have the ability to update book information, including title, author, category, and more. They can also upload a new book cover image.
- Delete Books: Books that are no longer needed in the collection can be easily removed from the catalog.
- Search Books: The app provides a search functionality that allows users to search for books by title. This feature simplifies the process of finding specific books in a large collection.
Stored XSS
Stored XSS vulnerability exists in add_book.php and update_book.php
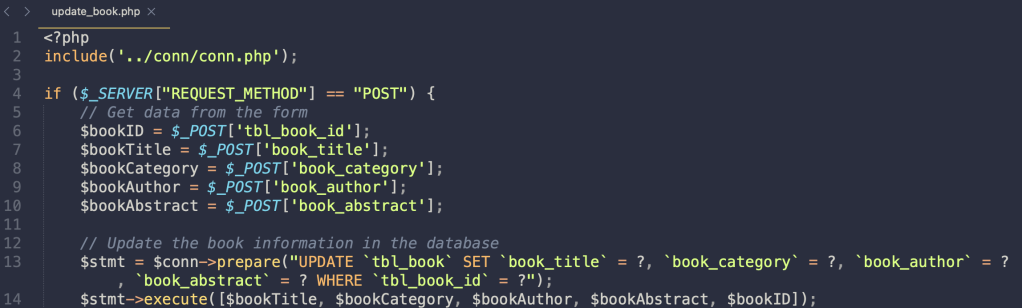
Although there are some validations in the code for uploaded image files (such as checking file type, size, and existence), no form of validation or cleaning is performed on other values obtained from $_POST variables (such as book_title, book_author, etc.)
Trying to insert unobfuscated XSS payloads in book_title and book_author
<script>alert(/xss/)</script>
Click Update Book and return to the home page


Refreshing the homepage, the XSS payload is still executed, confirming the Stored XSS vulnerability
This is attributed to CWE-79
SQL Injection
SQL Injection is a type of security vulnerability that enables attackers to interfere with the queries that an application makes to its database. It occurs when an application includes unsafe user input within a query. The attacker can then manipulate the query, leading to unauthorized data access, data modification, or even data deletion.
SQL vulnerability exists in delete_book.php, and the developer did not filter or validate the delete parameter.

<?php
include('../conn/conn.php');
if (isset($_GET['delete'])) {
$bookID = $_GET['delete'];
// Retrieve the book image filename
$stmt = $conn->prepare("SELECT `book_image` FROM `tbl_book` WHERE `tbl_book_id` = ?");
$stmt->execute([$bookID]);
$row = $stmt->fetch();
$bookImage = $row['book_image'];
// Delete the book from the database
$stmt = $conn->prepare("DELETE FROM `tbl_book` WHERE `tbl_book_id` = ?");
$stmt->execute([$bookID]);
// Delete the associated image file
if (!empty($bookImage)) {
$imagePath = "../image/" . $bookImage;
if (file_exists($imagePath)) {
unlink($imagePath);
}
}
// Redirect to the page where you want to display the updated book list
header("Location: http://localhost/book-catalog-app/index.php");
exit();
}
?>
Unsanitized input from a database flows into unlink, where it is used as a path. This may result in a Path Traversal vulnerability and allow an attacker to delete arbitrary files.
This is attributed to CWE-23

It can be seen that there is no verification or filtering of the delete parameter in the code.

Construct a malicious code that controls the delete parameter to delete the entire tbl_book table
1; DROP TABLE tbl_book;
The entire tbl_book table was deleted in its entirety, confirming the existence of a SQL injection vulnerability
This is attributed to CWE-89

コメントを投稿するにはログインしてください。